Firstly, I want to wish everyone a happy, prosperous, and secure 2020.
I have some personal news: I am excited to share that I am now part of the team at Axon Technologies.

Why Axon? :)
Because a new generation of cybersecurity companies is needed to fight the cyber threats in the Middle East and Africa. The Axon team is made up of global cybersecurity experts focused on improving cybersecurity maturity across the EMEA region. Our portfolio is across the cybersecurity value chain, and we are integrating detection, response, threat hunting, threat intelligence, and data sciences into a single cybersecurity offering aligned to industry standards and national regulatory frameworks. The pillars of Axon deliver the following (aligned to the NIST Cyber Security Framework high-level functions):

Axon’s approach to cybersecurity
Why Now?
The Threat Landscape
-
Nation-state threat actors: The Middle East, Africa, and GCC are facing a significantly increased cyber threat. Saudi Arabia for example with its size, wealth and geopolitical prominence is a prime target for cyber attackers, according to the Global Foundation for Cyber Studies and Research in Washington. In addition, there is a high probability that the recent geopolitical tensions in the region will lead to Iran increasing its offensive cyber-attacks against U.S. allies and U.S. interests in the region.
-
Financially motivated threat actors: We are seeing daily ransomware incidents and BEC threats, but unfortunately, companies are unaware of how to protect themselves or respond and recover from these incidents. Axon is here to help!
The Compliance Landscape
-
Regulators have a high level of sensitivity to the sovereignty of local network data and require organizations to ensure that all business, network, and particularly PII stays on in the country. We are seeing this across Saudi Arabia, and other GCC countries are following suit.
-
Saudi Vision 2030 stresses the need for improved cybersecurity across the Kingdom.
-
Aramco turning into a publicly traded global industrial conglomerate requires a strong and consistent cybersecurity framework across each of Aramco’s entities, associations, partners, and suppliers.
-
Saudi Vision 2030 calls for localised cybersecurity delivery through building national expertise in the Kingdom.
Axon Technologies will play a key role in helping to deliver Saudi Arabia’s Vision 2030 and its Digital Transformation Strategy through our globally recognised cybersecurity solutions delivered by local talent with full sovereignty of Saudi network data, ensuring all business, network, and particularly Personally Identifiable Information stays on Saudi soil.
Cyber Risk Exposure
-
No industry or company is immune from cyber-attacks.
-
The impact of a cyber-attack is more than just financial. There will be side effects on operations, reputation, brand and customer trust.
-
Key information assets, business processes, crown jewels need to be identified, prioritized and assessed for controls appropriate to the value of the asset.
-
Traditional controls are needed but not sufficient. No matter how many preventative controls a company invests in, technologies that help predict, detect, respond and remediate are needed in the fight against cybercrime.
-
Cloud is more prevalent in the Middle East market. Implementing appropriate and sufficient cybersecurity controls in cloud environments becomes a priority.
Traditional Strategies are not working
SIEMs
-
Built for Compliance — not Security
-
Average 15 months to fully implement, Ponemon institute 2016
-
Building, operating and managing costs 3–5x software expenditure, Ponemon 2016
MSSPs
-
Built for operational efficiency — not Security
-
One size fits all — they don’t get to know your crown jewels and your environment
-
Present alerts but don’t tell you how to respond and remediat
Security tools with machine learning modules
These tools monitor behaviours or rules that ingest troves of data. Generally, they attempt to identify malicious behaviour by firstly understanding normal behaviour. While this method can be helpful, we find that it is not working for several reasons:
- No ongoing ‘watering and feeding these tools’ — new behaviours, IOCs, configurations, detection mechanisms, playbooks, etc.
- By the time malicious activity has been detected, the breach often already happened.
- There is often a long backlog of incident investigations with little ability to prioritise.
- Monitoring for “divergence from normal behaviour” creates a huge number of false positives, wasting much of the investigation team’s time.
- Attackers today are utilising techniques that embody ‘normal’ behaviour.
- Collecting massive amounts of data creates privacy concerns and significant potential for abuse.
- Controls are not customized to critical assets, risks, actors, and actions and investigate steps and remediations are not well defined or tailored to individual incidents.
The Axon Difference
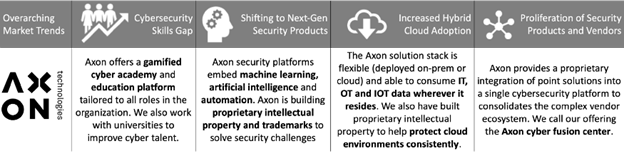
Alignment to global cybersecurity market trends
-
Axon is a company focused 100% on cybersecurity solutions.
-
Our team is unique in that it includes resources and skillsets not typically seen in cybersecurity companies — software developers(a team focused on developing integrations among the cybersecurity solutions at Axon and at our clients and building long term IP in the form of SaaS-based offerings), threat Intelligence researchers focused on the Middle East, GCC and Africa cyber threats and tactics, techniques and procedures (TTPs), senior intrusion analysis team carrying out advanced incident analysis and proactive threat hunting, incident response and incident management resources that are technical and understand security controls and architecture, security engineers that manage and optimise our technologies and platforms, data analysts focused on analysing raw data we collect to identify patterns and call out useful and actionable information for our clients — ‘finding the needle in the haystack’
-
We are building intellectual property using cloud-native infrastructure with artificial intelligence and data analytics modules to deliver a Software as a Service solution that brings together threat intelligence platform capabilities with a Security Orchestration, Automation and Response (SOAR) feature set in order to deliver a threat-based SOAR function to advanced customers.
-
We differentiate with our Cyber Institute capability. Our Cyber Institute is a gamified training platform that will help build a cybersecurity training curriculum and set of training modules for different roles across an organization (executives, IT teams, security specialists). We integrate a leaderboard capability and a ‘learning by doing’ concept into the security program.
-
We apply automation using an industry-leading SOAR platform with our custom-built playbooks and integrations in order to automate repeatable and time-consuming tasks (level 1 and some of level 2 tasks for security analysis), allowing our specialist team to focus on the serious incidents at our clients
-
We are constantly building detection rules, use cases, playbooks, and dashboards in our tools to ensure clients continuously see value in the services we deliver and to ensure our solutions are aligned to constantly optimised frameworks like MITRE ATT&CK.
-
We want to help clients at different levels of maturity, of different sizes and complexities, whether on-premise or in the cloud solve their cybersecurity challenges. We have the subject matter expertise, understanding of the threat landscape and are local across the Middle East and GCC!
-
Our service can be managed on the go for the ‘mobile customer’.
Our Approach
At Axon, we believe in the risk-based approach to cyber. We want to secure digital transformation initiatives for our clients without exposing them to more risk online. From our experience, a set of best-practice actions have emerged that we apply to all our engagements.
- We will look to fully embed cybersecurity in the enterprise-risk-management framework.
- We will help clients identify sources of business value and crown jewels (e.g., Intellectual property, payment processes, manufacturing process, etc.).
- We will look to understand the organisation’s cyber risk profile — across people, processes, and technology — internally and for third parties using well-established industry frameworks.
- We will identify and prioritise the threat actors relevant to each client, including their capabilities, motivations, and TTPs (based on the MITRE ATT&CK framework).
- We will identify any gaps in the current security controls environment and determine what actions are required to address the gaps.
- We will initiate a company-wide security training and awareness program tailored to different resources and critical roles at the client
- We will deploy our security operations fusion center services integrating detection, response, automation, hunting, and testing. Our services will continuously improve and optimise with the advancements in security technologies.
- We will build playbooks and detection rules tailored to the client’s environment and technologies and continuously review and optimise them.
- We will support incident response and investigations with on-site and remote specialist resources and tools.
- We will provide an ongoing monitoring and management capability of cyber efforts against risk appetite and deliver metrics and reports that align to the enterprise risk framework.
2020 and beyond
Our team’s view is the region needs a company like Axon Technologies to exist. The current cybersecurity industry across the Middle East is broken in so many ways. There is no standardised and consistent view of ‘what good looks like’ to reduce cyber risks and mitigate the threats. There is a huge variation in cybersecurity maturity levels across industries, regions, and company sizes. Companies are drowning in marketing materials and cybersecurity presentations that repeat similar messages around AI, machine learning, and threat intelligence. It becomes difficult to differentiate. Security providers are struggling to find and retain cyber talent. Training programs are available, but it is not easy to build the right curriculum for the right roles to secure the organisation.
I’ve got an incredibly challenging role as CEO to address the issues above and amazing colleagues, who are helping me achieve our goal and secure our clients.
My hope for this year is, as cyber defenders in the Middle East region, we can build communities to exchange information, share best practices and work together to better the industry and mitigate the threats.
If there’s anything me and my team can do to help you across your projects, feel free to reach out!
Here’s to 2020 and a successful year ahead for all of you!
Cheers,
Hadi, CEO Axon Technologies

