Introduction
Business Email Compromise (BEC) is a type of email cybercrime scam targeting companies and businesses (who conduct wire transfers and have suppliers abroad) to defraud them.
BEC is also known as Email Account Compromise (EAC), if executed correctly, the BEC scam can result in billions of dollars in potential losses as it is one of the most financially damaging online crimes.
BEC scam, formerly dubbed as Man-in-the-Email scam, heavily relies on social engineering tactics. Criminals utilize spoofed or compromised emails (through keyloggers or phishing attacks) to send email messages that appear to come from a known source making a legitimate request and ultimately performing fraudulent transfers.
Types of BEC Scams
According to the Federal Bureau of Investigation (FBI), there are 5 types of BEC scams:
- CEO Fraud
An attacker either gains access to a CEO’s email by using compromised email credentials (through a successful spear-phishing attack) or by spoofing the email address of the CEO and creating an email address that looks almost identical to the original with only slight variations. The attacker then contacts employees from the finance departments and asks for money transfers. - Account Compromise
The email account of a senior executive or employee is compromised and used to solicit invoice payments from vendors mentioned in their email contacts. The funds are subsequently transferred to bogus bank accounts. - False Invoice Scheme
Attackers pretend to be the suppliers of a certain company and request a fund transfer for payments to an account owned by fraudsters. The attack tactic usually targets companies with foreign suppliers. - Attorney Impersonation
The attacker impersonates a lawyer or other representative from the law firm in charge of sensitive and secret information. - Data Theft
HR can be targeted in order to obtain personal/sensitive information about employees/executives such as personally identifiable information (PII) or tax statements.
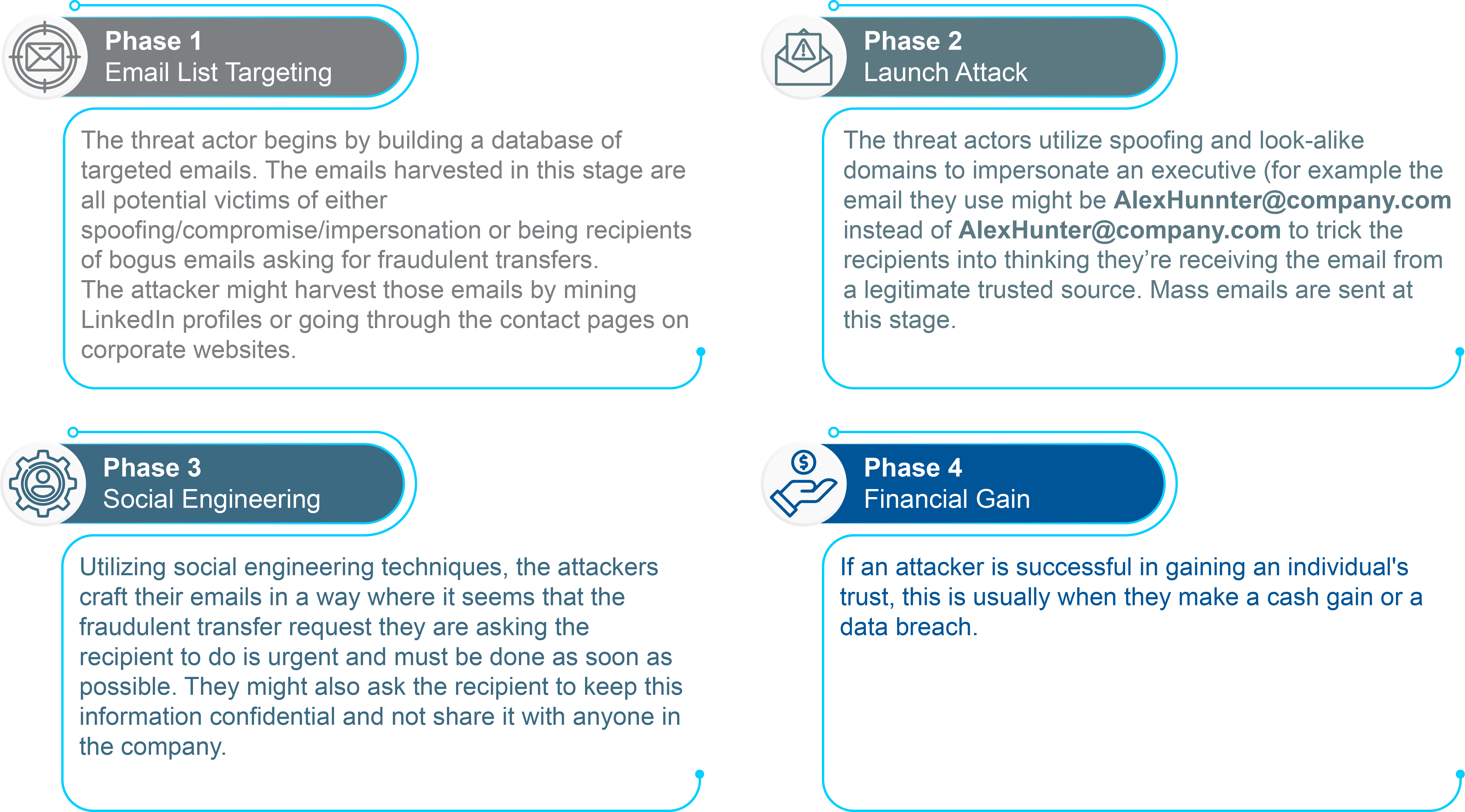
BEC Scam Phases
Protecting Yourself (and Your Company) Against BEC Scams
The following is a list of measures you can start taking today to lower the risk of a successful BEC scam:
- Enable two-factor authentication for all payment verification requests.
- Triple check the emails which are asking for the transfer of funds. Some scam emails may contain broken English, unusual date formats, and strange requests. Be vigilant.
- Create email rules which flag communications where the “reply” email address is different from the “from” email address.
- Create Intrusion Detection System Rules that flag emails with extensions similar to the company email.

How Axon Technologies Can Help
Axon Technologies is here to help you and your company in your cybersecurity journey by providing services such as:
- Training employees and making them proficient in differentiating between a legitimate email and a fraudulent one through effective email inspection techniques.
- Providing consultation services.
- Monitoring services are also available where our expert team of cyber defense analysts monitor your company networks and mailboxes to flag suspicious emails so they would not reach the intended recipient. In the unfortunate scenario where an incident had already taken place due to a successful BEC attack, our analyst would detect that an incident took place and escalate it to incident response.
- A fully capable incident response team ready to respond to any incident that could have taken place and carry out relevant investigations.

